 DeResistor @ USENIX Security 2023
DeResistor @ USENIX Security 2023
DeResistor: Toward Detection-Resistant Probing for Evasion of Internet Censorship
Abstract
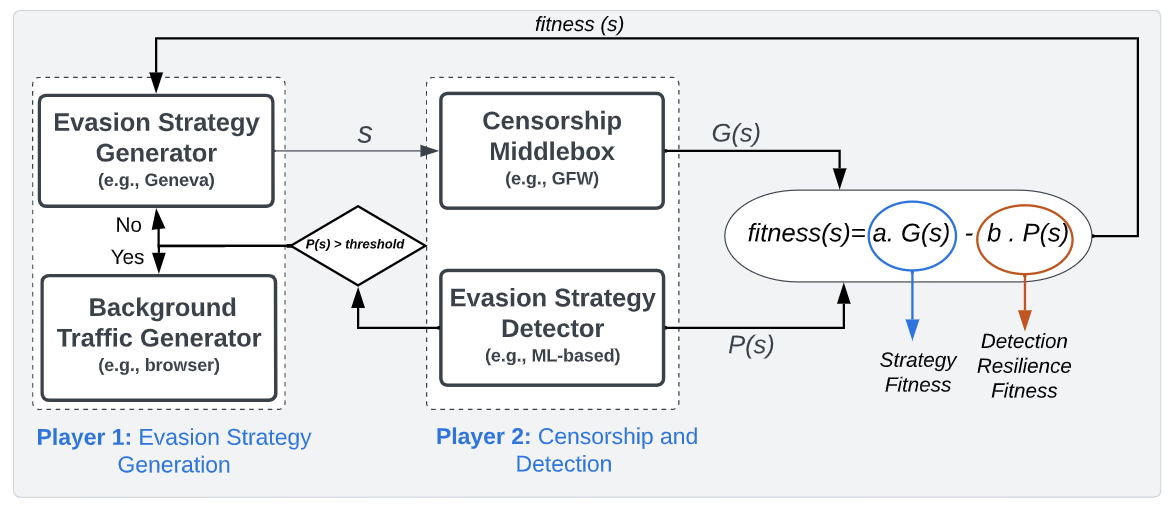
The arms race between Internet freedom advocates and censors has catalyzed the emergence of sophisticated blocking techniques and directed significant research emphasis toward the development of automated censorship measurement and In this paper, we however discover that probing censorship middleboxes using current evasion tools can be easily detected by censors, necessitating detection-resilient probing tools. We first develop a real-time detection approach that utilizes Machine Learning (ML) to detect flow-level packet-manipulation traces and an algorithm for IP-level detection based on Threshold Random Walk (TRW). We take the first steps toward detection-resilient censorship evasion by presenting DeResistor, a system that facilitates detection-resilient probing for packet-manipulation-based censorship evasion. DeResistor aims to defuse detection logic employed by censors by performing detection-guided pausing of censorship evasion attempts and interleaving them with normal user-driven network activity. We evaluate our techniques by leveraging Geneva, a state-of-the-art evasion strategy generator, and validate them against 11 simulated censors supplied by Geneva, while also testing them against real-world censors (i.e., China’s Great Firewall (GFW) and India). From an adversarial perspective, our proposed real-time detection method can quickly detect clients that attempt to probe censorship middleboxes with manipulated packets after inspecting only two probing flows. From a defense perspective, DeResistor is effective at shielding Geneva training from detection while enabling it to narrow the search space to produce less detectable traffic. Importantly, censorship evasion strategies generated using DeResistor can attain a high success rate from different vantage points against the GFW (up to 98% ) and 100% in India. Finally, we discuss detection countermeasures and extensibility of our approach to other censor-probing-based tools.