 SLEUTH
SLEUTH
Abstract
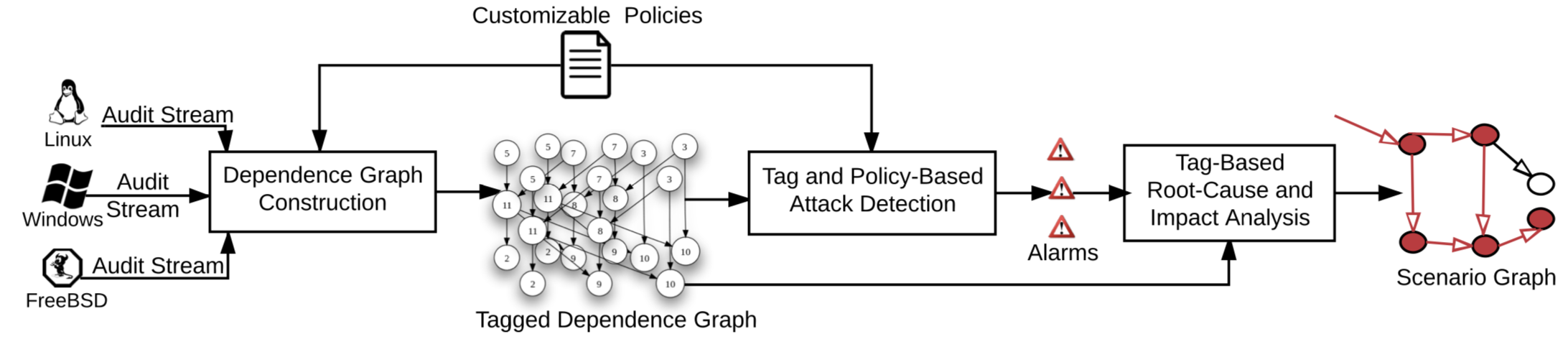
We present an approach and system for real-time recon- struction of attack scenarios on an enterprise host. To meet the scalability and real-time needs of the problem, we develop a platform-neutral, main-memory based, de- pendency graph abstraction of audit-log data. We then present efficient, tag-based techniques for attack detec- tion and reconstruction, including source identification and impact analysis. We also develop methods to reveal the big picture of attacks by construction of compact, vi- sual graphs of attack steps. Our system participated in a red team evaluation organized by DARPA and was able to successfully detect and reconstruct the details of the red team’s attacks on hosts running Windows, FreeBSD and Linux.
Type
Publication
Proceedings of the 26th USENIX Security Symposium (SEC)